Due: Wednesday, December 4, 2013, 23:59
Problem 1
In A. Barth and C. Jackson's paper Beware of Finer-grained Origins, they propose three solutions to the problem of finer-grained origin policies interacting poorly with the browser's same origin policy for JavaScript. Which of their solutions has been adopted? Briefly defend your claim.
Problem 2
The ZeuS trojan is installed on many compromised machines, and allows these machines to be controlled as part of a botnet. ZeuS includes a keylogger component that harvests users’ banking information when they log in to e-banking sites: account numbers, passwords, and other details.
In addition, recent versions of ZeuS can change the Bank of America login procedure as it is perceived by users on ZeuS-infected machines. In addition to the usual SiteKey authentication, users on ZeuS-infected machines who try to log into Bank of America’s e-banking site will need to answer questions like, “What was your first pet’s name?” (Bank of America will itself sometimes ask such questions; ZeuS copies the Bank of America UI.) The ZeuS management interface allows the botnet owner to specify the questions to be asked and to harvest users’ answers along with other stolen information.
Why would an attacker want to inject such questions into the Bank of America login procedure? Why would users answer them?
Problem 3
The most commonly used keyed lock is a pin tumbler lock, shown in Figure 1. This type of lock features k pin stacks (typically 4 to 7, with the lock in the figure having 6), each cut at one of n possible depths (typically 4 to 10), which are held in the plug by springs.
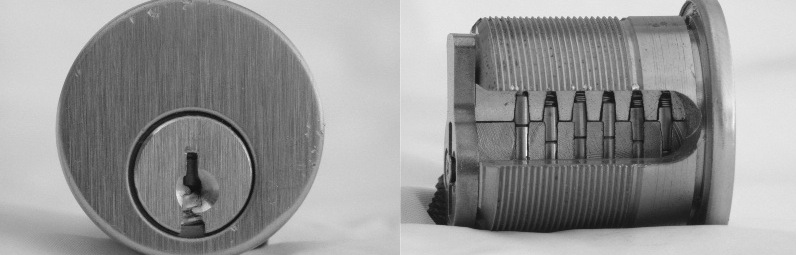 |
Figure 1. On the left, the lock face. On the right, a cutaway view showing six pin stacks and (horizontal) shear line. The pin stacks keep the plug from rotating within the shell and opening the door.
A key has bittings at a certain depth for each pin stack. When the key is inserted into the keyway, its bittings push each pin stack up by a certain amounts. The correct key will cause each to be pushed so that its cut aligns with the shear line that separates the plug from the shell, allowing the plug to rotate, as shown in Figure 2.
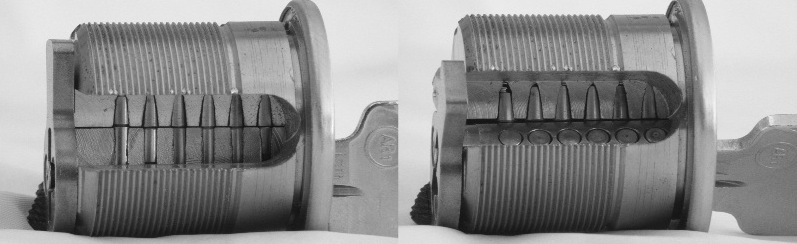 |
Figure 2. On the left, a cutaway view showing the correct key inserted in the lock. Note that the cuts in the pin stacks are aligned with the shear line. This allows the plug to rotate, as shown on the right.
In many institutional settings a master-keying system is used, where each of several locks (say, one for each room in a dorm) has a different change key, but all share a single master key. This is most commonly implemented by including two cuts in each pin stack, one for the change key, the other for the master key, as shown in Figure 3. The locks will each have different change cuts, but all share the same master cuts, so the same master key will open all of them. The change key and the master key never share a cut: in each pin stack there is one cut for the change key, and another at a different depth (either above or below) for the master key.
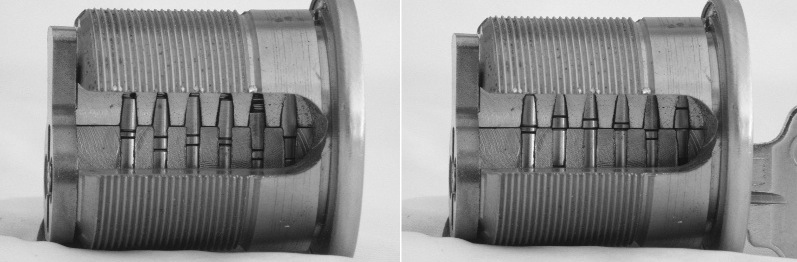 |
Figure 3. On the left, a cutaway view of a master-keyed lock. Note that each pin stack has two cuts. On the right, the lock with the change (non-master) key inserted. One set of cuts is at the shear line; the other cut for each stack is either above or below.
Suppose that a lock is keyed with the change key at 11111 (five pins, all at depth 1), and the master key at 44444 (five pins again, all at depth 4 this time). Will a key cut at 11411 open the lock? Explain.
Suppose you have access to a master-keyed lock, a change key that opens it, but not the master key. In addition, you have a supply of blanks that can be filed down to specific bittings of your choice. Explain how to use the observation from part 1 to recover the master key.
Suppose you have access to the change keys for many locks all keyed for the same master key (but, again, no access to the master key). For example, suppose that you measure the bitting on the keys given all the residents in a dorm. Explain how you can (with high probability) recover the master key without any blanks — and even without access to any of the locks! (This was actually done at the CRYPTO conference a number of years ago.)